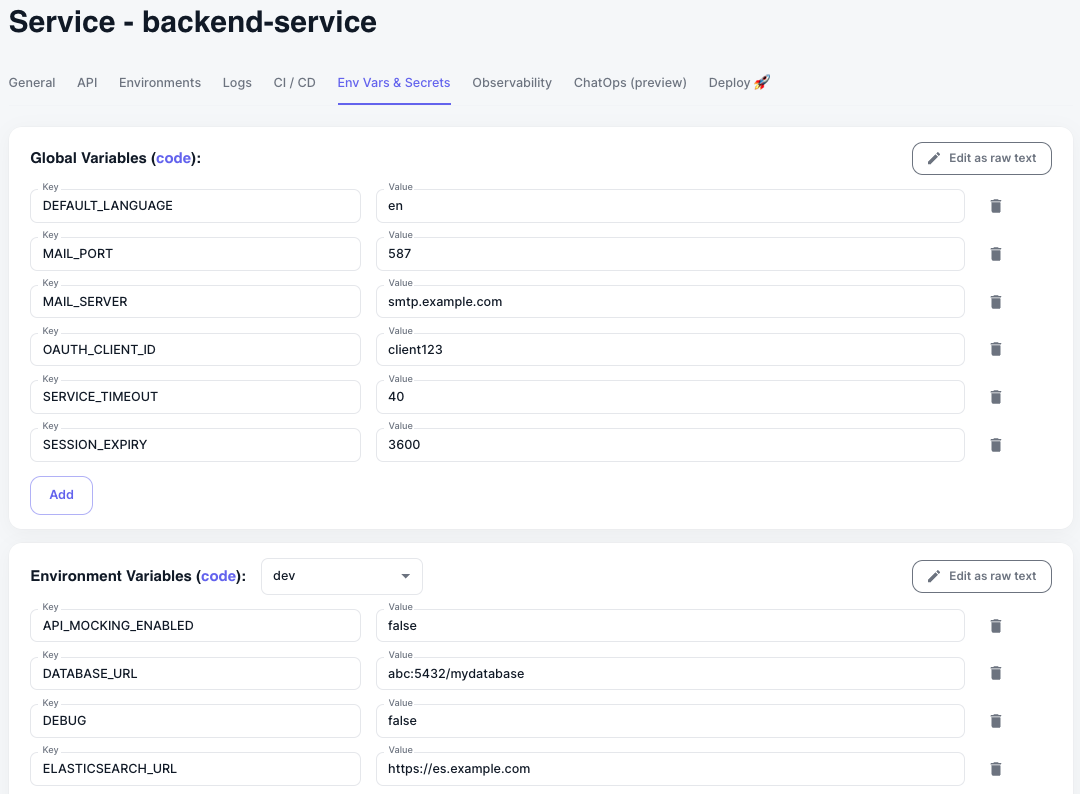
Per Service Global and Env Variables
Koala utilizes two types of variables:- Global Service Variables: Shared variables that are available to your service across all environments.
- Environment Service Variables: Per environment variables that are specific to your service in a particular environment (e.g., development, staging, production).
Secrets Management with Sealed Secrets
Koala leverages the popular bitnami-labs/sealed-secrets project to ensure secure secret storage. Sealed Secrets encrypts sensitive data like API keys and passwords before storing them in your code repository. This encryption protects your secrets even if your repository is compromised. During deployment, the Sealed Secret is included with other resources. The Sealed Secrets controller uses a private key to decrypt it, converting it into a usable Secret for your application pods. Koala, lacking access to this private key, encrypts the secret with the public key. Decryption occurs within your k8s clusters, ensuring Koala cannot access your secrets. This approach offers several advantages, with the primary benefit being robust version control for your secrets. Sealed Secrets allow you to:- Track changes to secrets over time.
- Revert to previous configurations if necessary.
- Identify who made specific modifications.
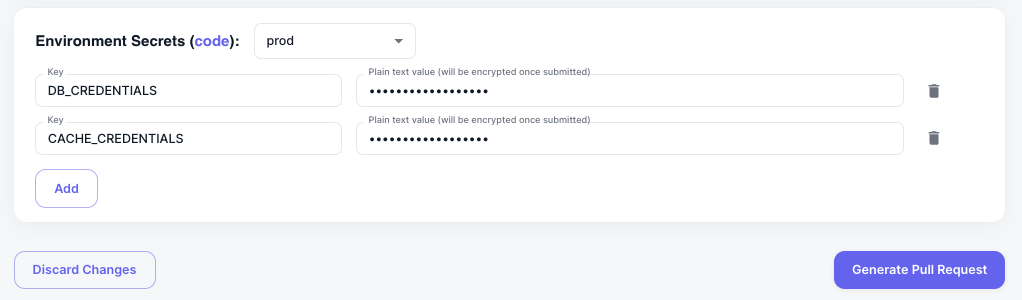
Managing Secrets in Koala
Managing secrets with Koala is remarkably straightforward.- Locate the “Environment Secrets” section within the “Env Vars & Secrets” tab for your service.
- Add or edit your secrets as needed.
- Click on “Generate Pull Request” to integrate the secrets into your repository.
- Delete the previous key (using the trash bin icon).
- Re-add it on a new line.
- Generate a new pull request.
Prerequisites for Sealed Secrets
To leverage sealed secrets, you must have bitnami-labs/sealed-secrets installed on all relevant clusters. The recommended approach is installation via the Koala ArgoCD Control Plane, although manual installation is also an option. Installation using Koala Control Plane:- Install ArgoCD on your management Kubernetes cluster following the interactive installation instructions. This is a brief manual process, allowing ArgoCD to manage additional add-ons for your clusters.
- Install the Sealed Secrets addon: Navigate to the Manage Cluster Addons section within the Koala UI. Choose the “Sealed Secrets controller” addon and select the clusters where you want your secrets to be accessible (typically all clusters). Koala offers a default configuration for the addon, but you can modify it directly in the UI if required.
Enabling Automatic Reloading on Config Updates
KoalaOps supports Reloader, an automation tool that ensures your deployments always run with the latest configurations when environment variables or secrets change. By default, Kubernetes does not restart pods when ConfigMaps or Secrets are updated, requiring manual intervention. Reloader solves this by automatically triggering a rolling restart of affected services.How It Works
- Monitors ConfigMaps and Secrets for changes.
- Automatically triggers a rolling restart for deployments, statefulsets, and daemonsets when changes are detected.
- Ensures your services are always running with the latest configurations without needing manual restarts.
Why Use Reloader?
- Eliminates manual restarts when updating environment variables or secrets.
- Improves automation in CI/CD workflows and GitOps-based deployments.
- Ensures configuration consistency across Kubernetes environments.
Enabling Reloader Per Service
To enable automatic reloading for a specific service:- Navigate to the Environment Variables and Secrets section in the service configuration.
- Scroll down and toggle Reload on Environment Variables or Secrets Update.
- Click Apply
- This ensures that the service automatically restarts whenever its environment variables or secrets change.
Prerequisites: Enabling the Reloader Add-on
Before using this feature, the Reloader add-on must be installed on the relevant Kubernetes clusters:- Go to the Control Plane section.
- Select the GitOps tab.
- Locate Reloader under the Featured Addons.
- Generate the required pull requests to enable Reloader for the relevant clusters.
